← what does the ioc stand for what does ioc stand for in security? what is an ioc cybersecurity What are indicators of compromise (ioc)? →
If you are looking for Unraveling the Complexity: IOC Cybersecurity Explained - CyberExperts.com you've came to the right page. We have 35 Pics about Unraveling the Complexity: IOC Cybersecurity Explained - CyberExperts.com like Indicators of Compromise: Cybersecurity’s Digital Breadcrumbs - Hashed, What are Indicators of Attack (IOAs)? How they Differ from IOCs | UpGuard and also Understanding Indicator of Compromise (IoC) in Cybersecurity: Signs and. Here it is:
Unraveling The Complexity: IOC Cybersecurity Explained - CyberExperts.com
 cyberexperts.com
cyberexperts.com
Unraveling the Complexity: IOC Cybersecurity Explained - CyberExperts.com
Importance Of Indicators Of Compromise (IoCs) In CTI For Actionable
 socradar.io
socradar.io
Importance of Indicators of Compromise (IoCs) in CTI for Actionable ...
Mastering IOC Cybersecurity: A Tech Enthusiast Perspective
 cyberexperts.com
cyberexperts.com
Mastering IOC Cybersecurity: A Tech Enthusiast Perspective ...
What Is IOC In Cyber Security Examples? - Darwin's Data
 darwinsdata.com
darwinsdata.com
What is IOC in cyber security examples? - Darwin's Data
IoC In Computing: Role And Functions Of Indicators Of Compromise
 4imag.com
4imag.com
IoC in computing: role and functions of indicators of compromise
IOC Vs IOA: #1 Cybersecurity Strategy & Threat Intelligence
 blueteamresources.in
blueteamresources.in
IOC vs IOA: #1 Cybersecurity Strategy & Threat Intelligence
Indicators Of Compromise: Cybersecurity’s Digital Breadcrumbs - Hashed
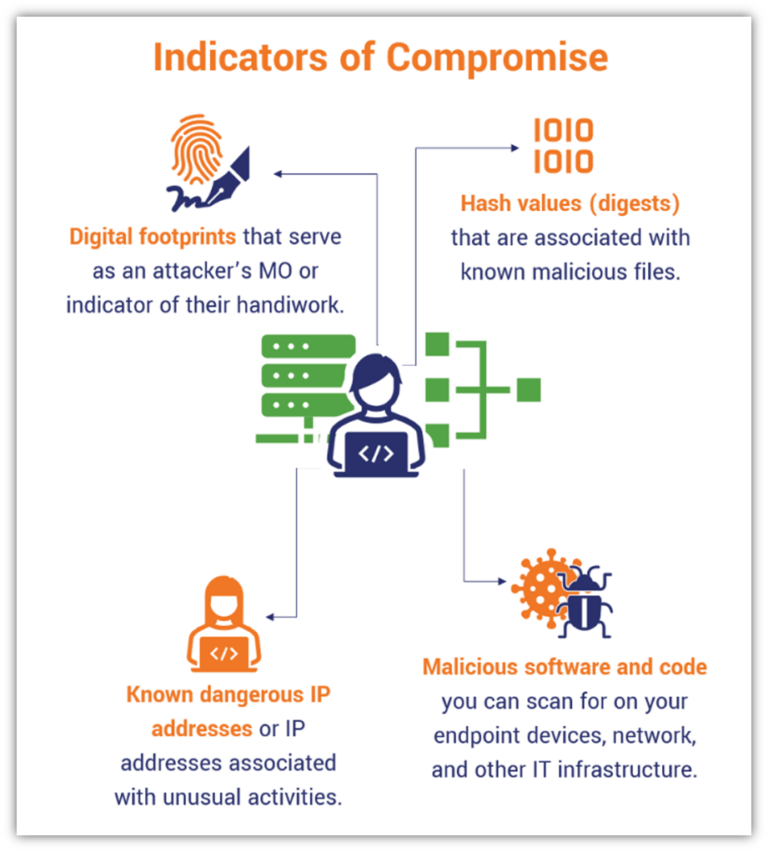 www.thesslstore.com
www.thesslstore.com
Indicators of Compromise: Cybersecurity’s Digital Breadcrumbs - Hashed ...
Understanding Indicator Of Compromise (IoC) In Cybersecurity: Signs And
 www.csocanalyst.com
www.csocanalyst.com
Understanding Indicator of Compromise (IoC) in Cybersecurity: Signs and ...
Indicators Of Compromise: Cybersecurity’s Digital Breadcrumbs - Hashed
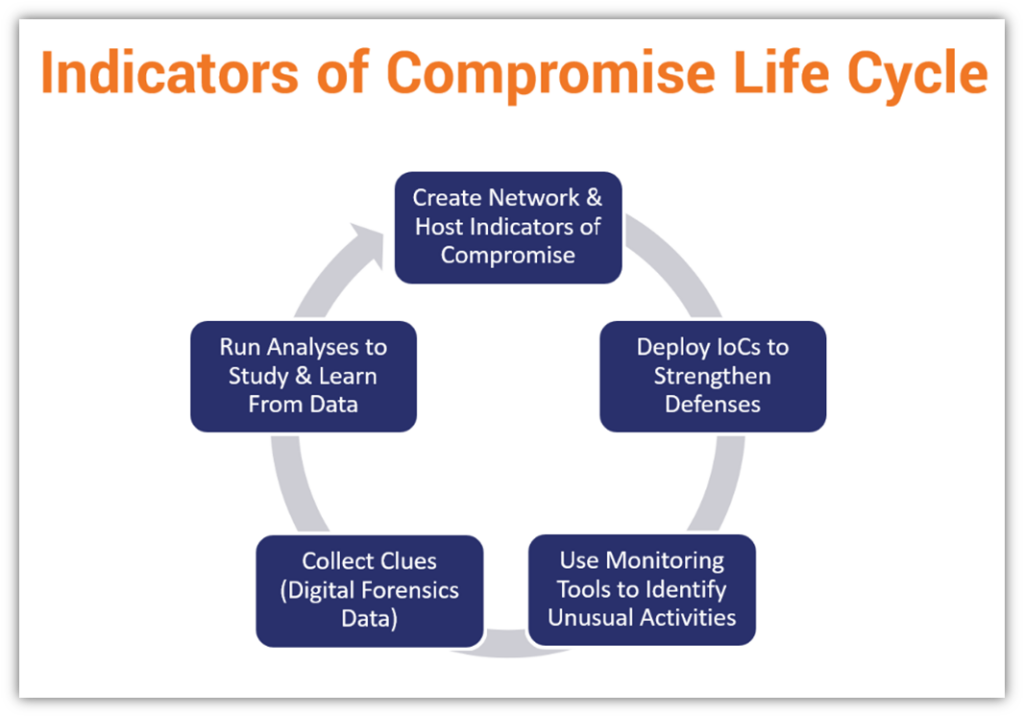 www.thesslstore.com
www.thesslstore.com
Indicators of Compromise: Cybersecurity’s Digital Breadcrumbs - Hashed ...
What Are Indicators Of Attack (IOAs)? How They Differ From IOCs | UpGuard
 www.upguard.com
www.upguard.com
What are Indicators of Attack (IOAs)? How they Differ from IOCs | UpGuard
Cybersecurity IOC Advisory: Understanding And Mitigating The Threat Of
 www.linkedin.com
www.linkedin.com
Cybersecurity IOC Advisory: Understanding and Mitigating the Threat of ...
Unraveling The Complexity: IOC Cybersecurity Explained - CyberExperts.com
 cyberexperts.com
cyberexperts.com
Unraveling the Complexity: IOC Cybersecurity Explained - CyberExperts.com
IoCs چیست؟ | نحوه کار IoC به چه شکل میباشد؟ | تفاوت بین IoCs و IoAs
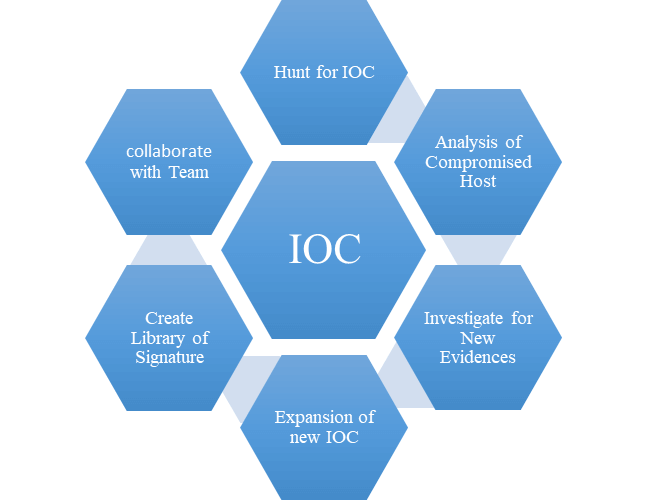 motakhasessho.ir
motakhasessho.ir
IoCs چیست؟ | نحوه کار IoC به چه شکل میباشد؟ | تفاوت بین IoCs و IoAs ...
Indicators Of Compromise (IOCs): How We Collect And Use Them | Securelist
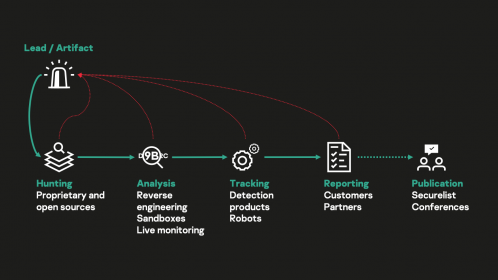 securelist.com
securelist.com
Indicators of compromise (IOCs): how we collect and use them | Securelist
What Is Indicator Of Compromise (IOC) In Cyber Security | E-SPIN Group
 www.e-spincorp.com
www.e-spincorp.com
What is indicator of compromise (IOC) in cyber security | E-SPIN Group
Improve SOC Efficiency With Intelligence-Powered Security Operations
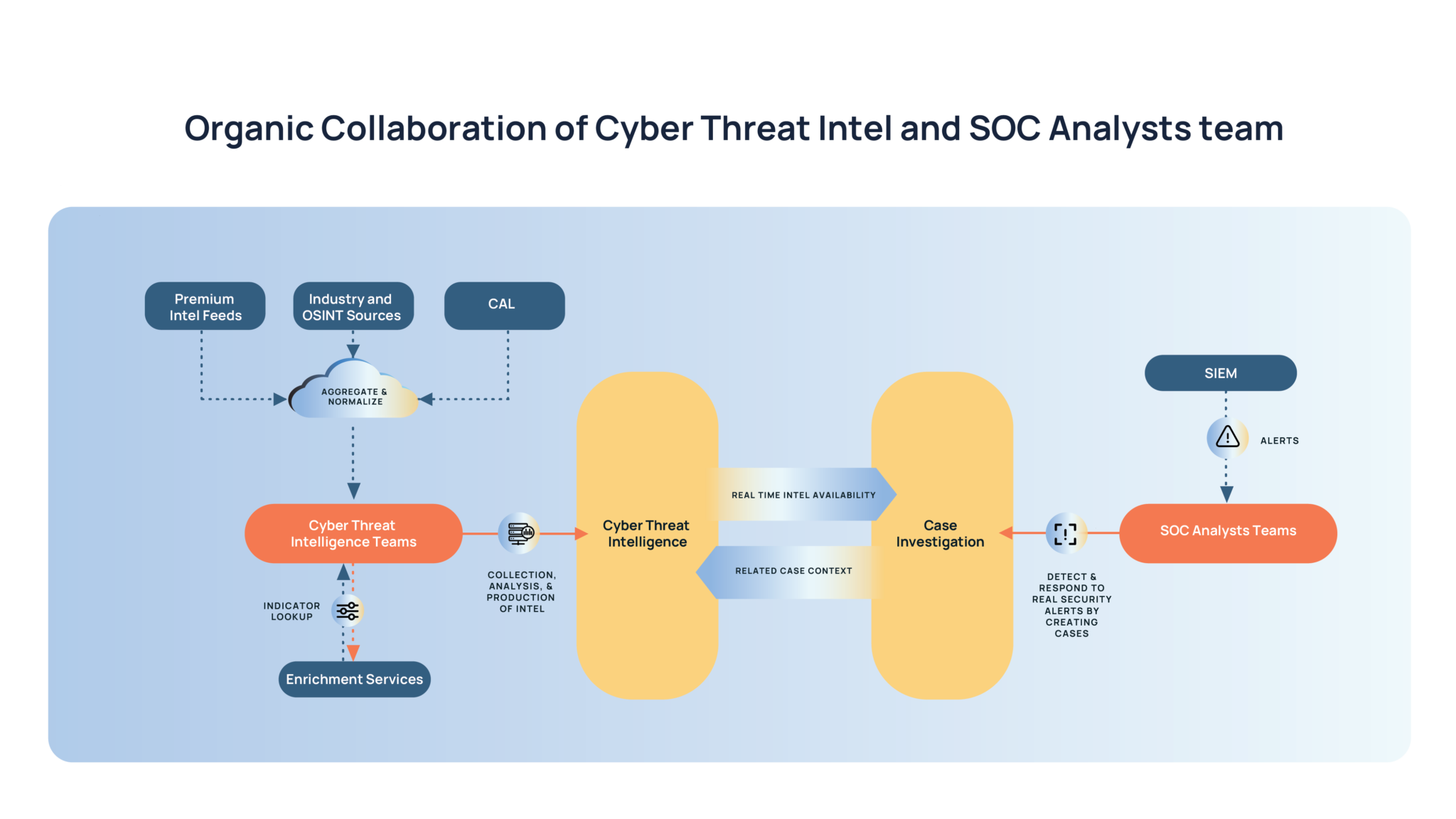 threatconnect.com
threatconnect.com
Improve SOC Efficiency with Intelligence-Powered Security Operations ...
Importance Of IOC Detection Rules
 www.talanoscybersecurity.com
www.talanoscybersecurity.com
Importance of IOC Detection Rules
IOA Vs IOC In Cyber Defense: Unraveling The Key Distinctions
 www.tatacommunications.com
www.tatacommunications.com
IOA vs IOC in Cyber Defense: Unraveling the Key Distinctions
Mastering IOC Cybersecurity: A Tech Enthusiast Perspective
 cyberexperts.com
cyberexperts.com
Mastering IOC Cybersecurity: A Tech Enthusiast Perspective ...
What Are Indicators Of Compromise (IOC) In Cyber Security? - Intellipaat
 intellipaat.com
intellipaat.com
What are Indicators of Compromise (IOC) in Cyber Security? - Intellipaat
Indicators Of Compromise: Cybersecurity’s Digital Breadcrumbs - Hashed
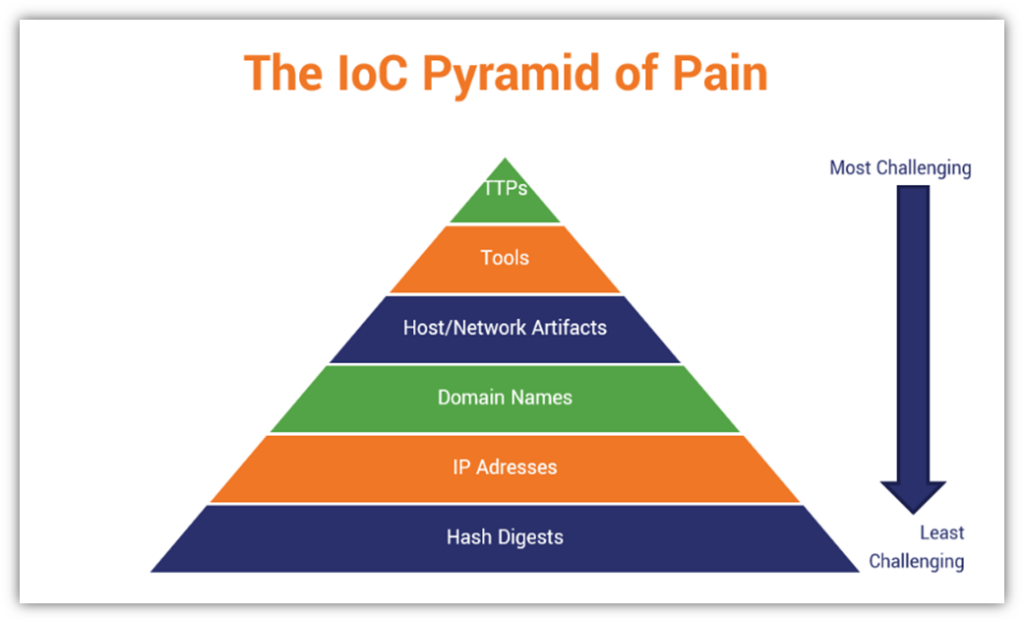 www.thesslstore.com
www.thesslstore.com
Indicators of Compromise: Cybersecurity’s Digital Breadcrumbs - Hashed ...
IOAs Und IOCs Im Vergleich | CrowdStrike
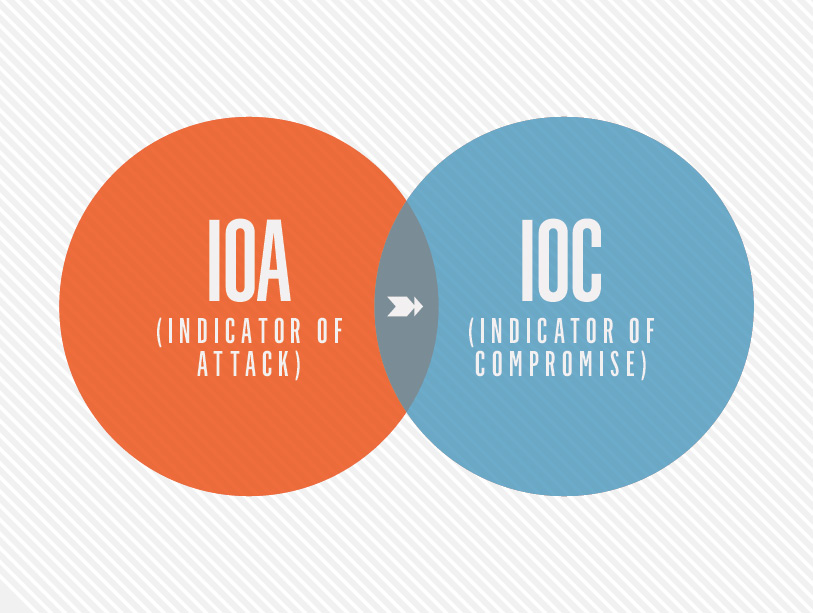 www.crowdstrike.de
www.crowdstrike.de
IOAs und IOCs im Vergleich | CrowdStrike
IOC Vs IOA | Explained By Cyber Security Professional - YouTube
 www.youtube.com
www.youtube.com
IOC vs IOA | Explained by Cyber security Professional - YouTube
Detecting And Responding To Cyber Threats Effectively
 harshji.com
harshji.com
Detecting and Responding to Cyber Threats Effectively
Mastering IOC Cybersecurity: A Tech Enthusiast Perspective
 cyberexperts.com
cyberexperts.com
Mastering IOC Cybersecurity: A Tech Enthusiast Perspective ...
What Are Indicators Of Compromise (IOC) In Cyber Security? - Intellipaat
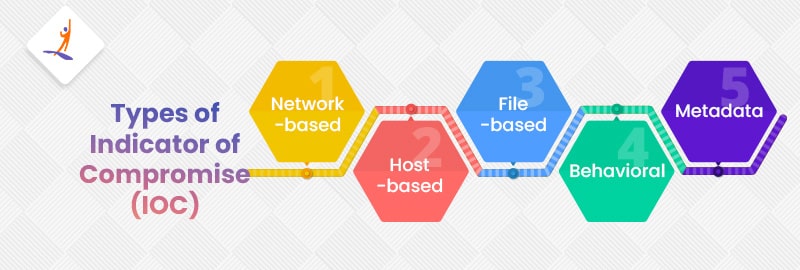 intellipaat.com
intellipaat.com
What are Indicators of Compromise (IOC) in Cyber Security? - Intellipaat
Identifying A Breach: Finding Indicators Of Compromise (IOC)
 virtualarmour.com
virtualarmour.com
Identifying a Breach: Finding Indicators of Compromise (IOC)
What Are Indicators Of Compromise? IOC Explained - Zenarmor.com
 www.zenarmor.com
www.zenarmor.com
What are Indicators of Compromise? IOC Explained - zenarmor.com
What Is IOC In Cyber Security? - Logsign
 www.logsign.com
www.logsign.com
What is IOC in Cyber Security? - Logsign
Unleashing The Power Of IoCs In Cybersecurity
 www.neumetric.com
www.neumetric.com
Unleashing the Power of IoCs in Cybersecurity
Importance Of Indicators Of Compromise (IoCs) In CTI For Actionable
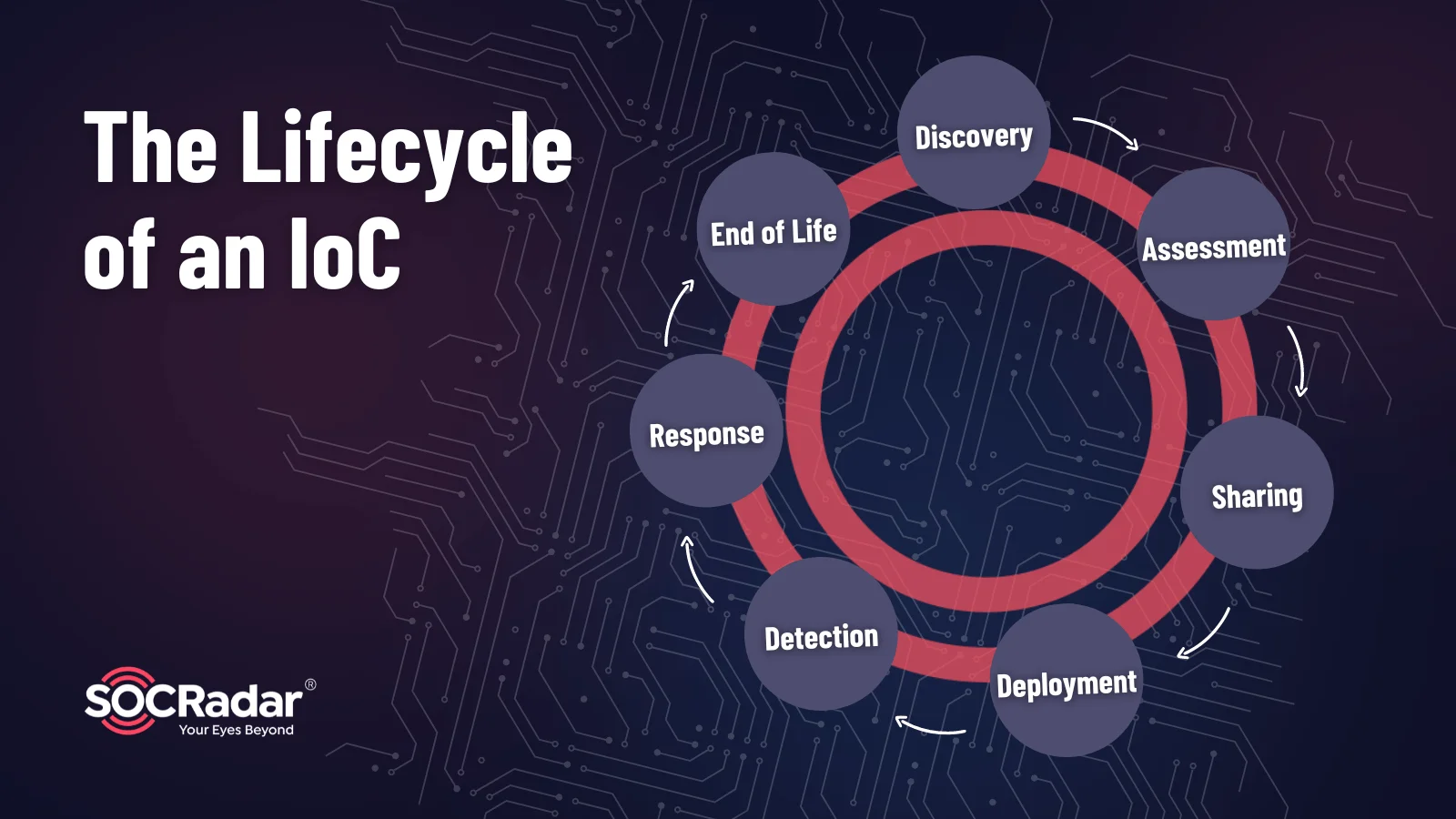 socradar.io
socradar.io
Importance of Indicators of Compromise (IoCs) in CTI for Actionable ...
Mastering IOC Cybersecurity: A Tech Enthusiast Perspective
 cyberexperts.com
cyberexperts.com
Mastering IOC Cybersecurity: A Tech Enthusiast Perspective ...
What Are Indicators Of Attack (IOAs)? How They Differ From IOCs | UpGuard
 www.upguard.com
www.upguard.com
What are Indicators of Attack (IOAs)? How they Differ from IOCs | UpGuard
Unraveling The Complexity: IOC Cybersecurity Explained - CyberExperts.com
 cyberexperts.com
cyberexperts.com
Unraveling the Complexity: IOC Cybersecurity Explained - CyberExperts.com
Mapping ZveloCTI To The Pyramid Of Pain IOCs For IR & Threat Hunting (2022)
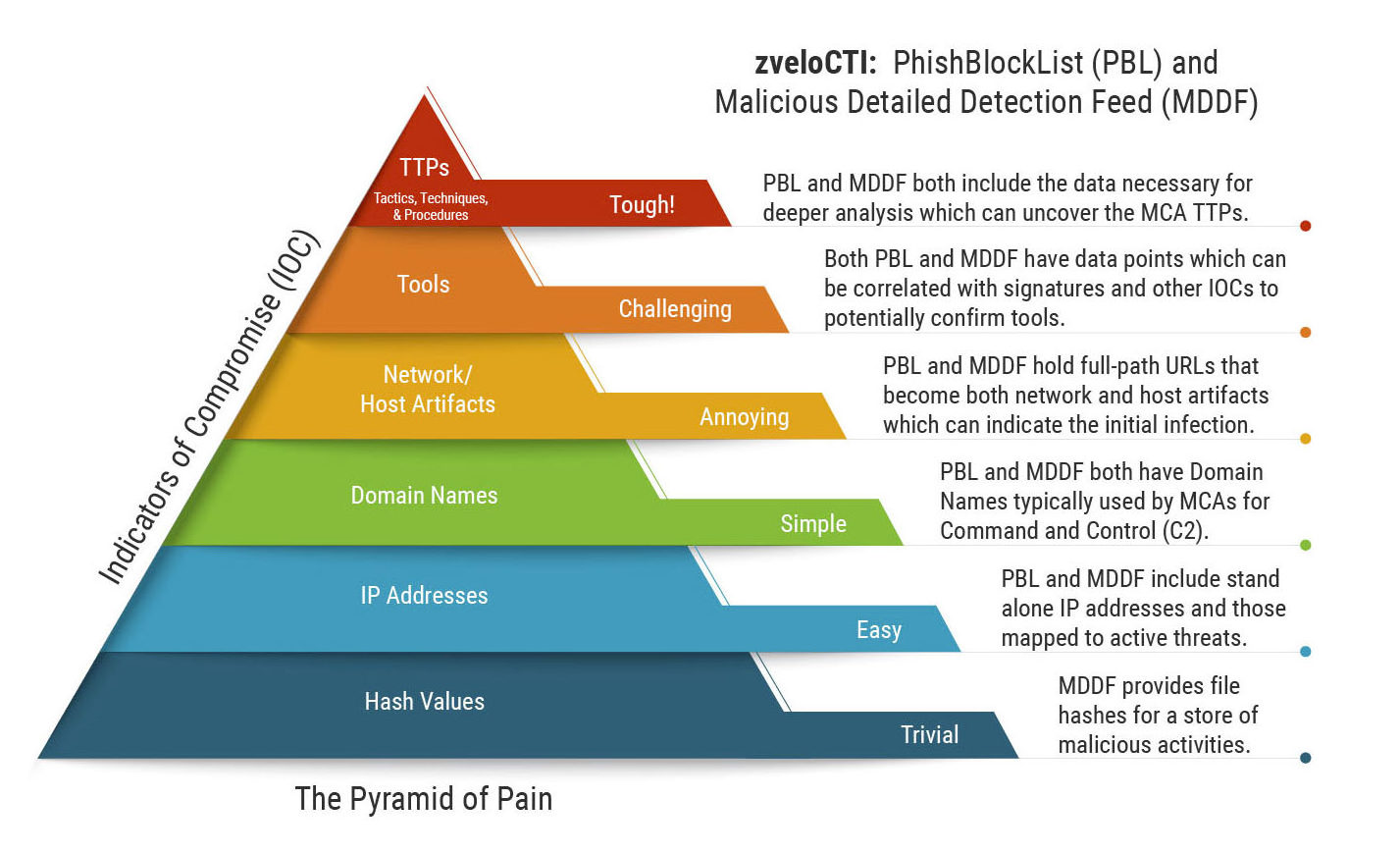 otarbo.com
otarbo.com
Mapping zveloCTI to the Pyramid of Pain IOCs for IR & Threat Hunting (2022)
ioc in computing: role and functions of indicators of compromise. Mastering ioc cybersecurity: a tech enthusiast perspective .... Mastering ioc cybersecurity: a tech enthusiast perspective