← cyber security jobs united states Careers in cybersecurity usa jobs cybersecurity jobs remote How to find the best remote cyber security jobs in 2021? insights on →
If you are looking for Frontiers | Handling User-Oriented Cyber-Attacks: STRIM, a User-Based you've visit to the right page. We have 35 Pictures about Frontiers | Handling User-Oriented Cyber-Attacks: STRIM, a User-Based like What is Vulnerability in Cyber Security With Example?, Research Group Cyber Security | HU University of Applied Sciences Utrecht and also Cybersecurity Program - University of Idaho. Read more:
Frontiers | Handling User-Oriented Cyber-Attacks: STRIM, A User-Based
 www.frontiersin.org
www.frontiersin.org
cyber attack attacks oriented handling autopsy computer strim
Cybersecurity Awareness Month: A Call To Action For Businesses
 www.pulsetechnology.com
www.pulsetechnology.com
Cyber Security In Universities | Threats, Threat Actors And Defense
 thecyphere.com
thecyphere.com
Department Of Cyber Security And Digital Forensics | Bhubaneswar Campus
 bhubaneswar.nfsu.ac.in
bhubaneswar.nfsu.ac.in
What Do You Do If A Hacker Takes Control Of Your Ship?
 channel16.dryadglobal.com
channel16.dryadglobal.com
What Is Cybersecurity? - Nuformat
 www.nuformat.com
www.nuformat.com
cybersecurity
Government Cyber Security Strategy 2022-2030 - Matrix
 matrixni.org
matrixni.org
How The Rise Of Machine Identities Is Reshaping Cybersecurity
 www.msn.com
www.msn.com
DOD Releases Path To Cyber Security Through Zero Trust Architecture > U
 www.defense.gov
www.defense.gov
Research Group Cyber Security | HU University Of Applied Sciences Utrecht
 www.internationalhu.com
www.internationalhu.com
Study Cyber Security At University Of Huddersfield - NCUK
 www.ncuk.ac.uk
www.ncuk.ac.uk
cyber ncuk huddersfield
Department Of Cyber Security & Digital Forensics | Bhubaneswar Campus, NFSU
 bhubaneswar.nfsu.ac.in
bhubaneswar.nfsu.ac.in
University Of Idaho Cybersecurity – CollegeLearners.com
 collegelearners.com
collegelearners.com
Programs | Bhubaneswar Campus, NFSU
 bhubaneswar.nfsu.ac.in
bhubaneswar.nfsu.ac.in
Cybersecurity Program - University Of Idaho
 www.uidaho.edu
www.uidaho.edu
cybersecurity engr uidaho
HU Places Among The 10 Best For Its Cybersecurity Offerings
 www.harrisburgu.edu
www.harrisburgu.edu
Cyber Security Policies: Importance And Types
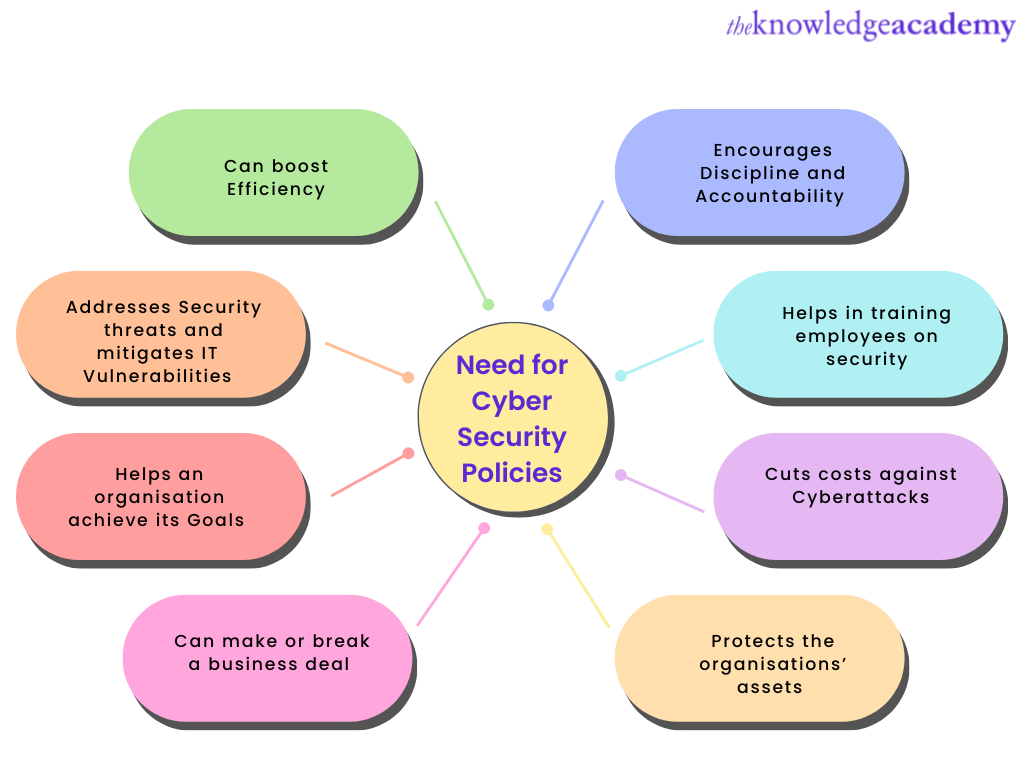 www.theknowledgeacademy.com
www.theknowledgeacademy.com
Department Of Cyber Security & Digital Forensics | Bhubaneswar Campus, NFSU
 bhubaneswar.nfsu.ac.in
bhubaneswar.nfsu.ac.in
University Of Houston Joins Consortium To Enhance Cybersecurity
 www.uh.edu
www.uh.edu
CyberSecurity - UH IEEE Presentation 2015-04 | PPT
 www.slideshare.net
www.slideshare.net
Cyber Security Education Dave Stevens UHCC Cyber Security
 slidetodoc.com
slidetodoc.com
UH Cybersecurity Club (@UH_Cyber) | Twitter
 twitter.com
twitter.com
What Is Vulnerability In Cyber Security With Example?
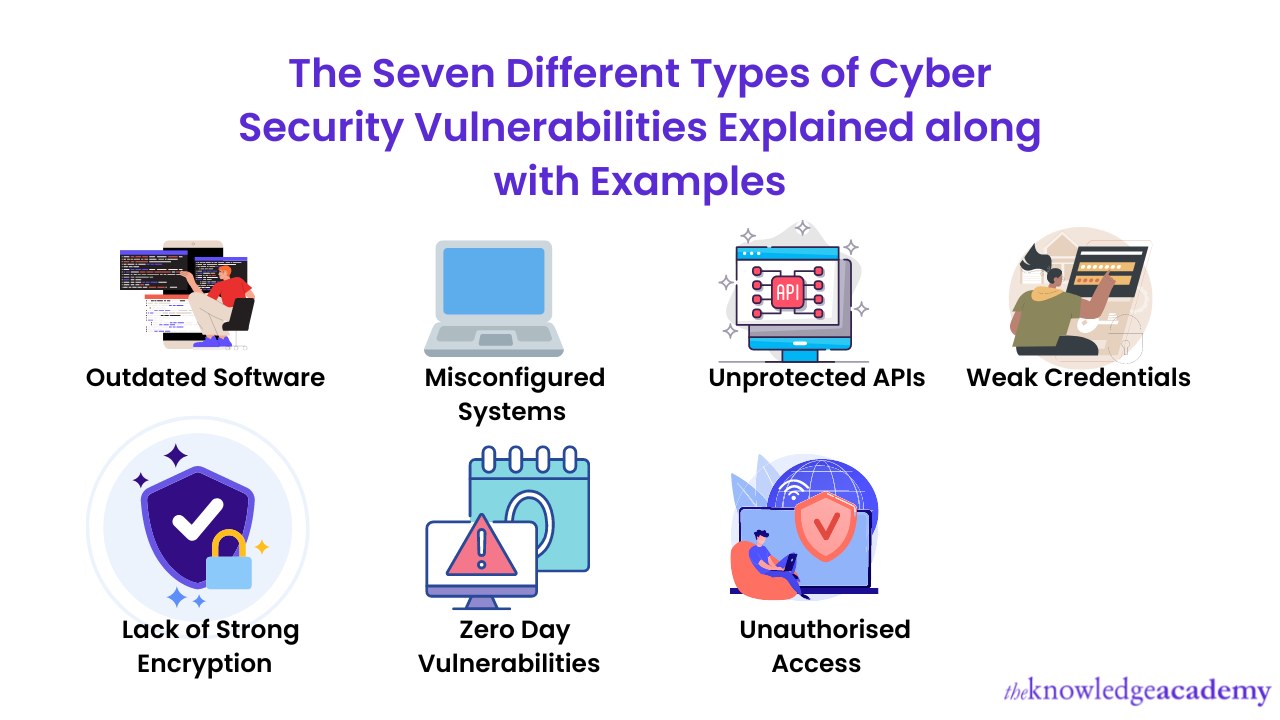 www.theknowledgeacademy.com
www.theknowledgeacademy.com
Cybersecurity Process Improvement: Applying Lean Principles To
 www.linkedin.com
www.linkedin.com
HU Hosts Cybersecurity Summit Aimed At Tackling Industry Challenges
 www.harrisburgu.edu
www.harrisburgu.edu
Cybersecurity | Homeland Security
 www.dhs.gov
www.dhs.gov
dhs cyber cybersecurity security homeland infrastructure protecting securing attacks representation science networks
1920x1080xe6e7& Resolution Cybersecurity Core 1080P Laptop Full HD
 wallpapersden.com
wallpapersden.com
Online Bachelor Of Applied Science In Applied Cybersecurity | Edwards
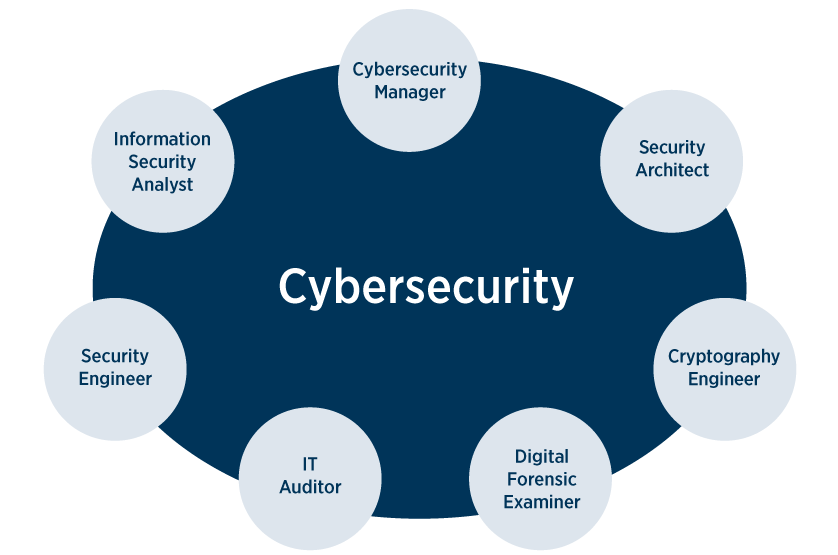 edwardscampus.ku.edu
edwardscampus.ku.edu
Department Of Cyber Security And Digital Forensics | Bhubaneswar Campus
Important Cybersecurity Terms You Should Know In 2023
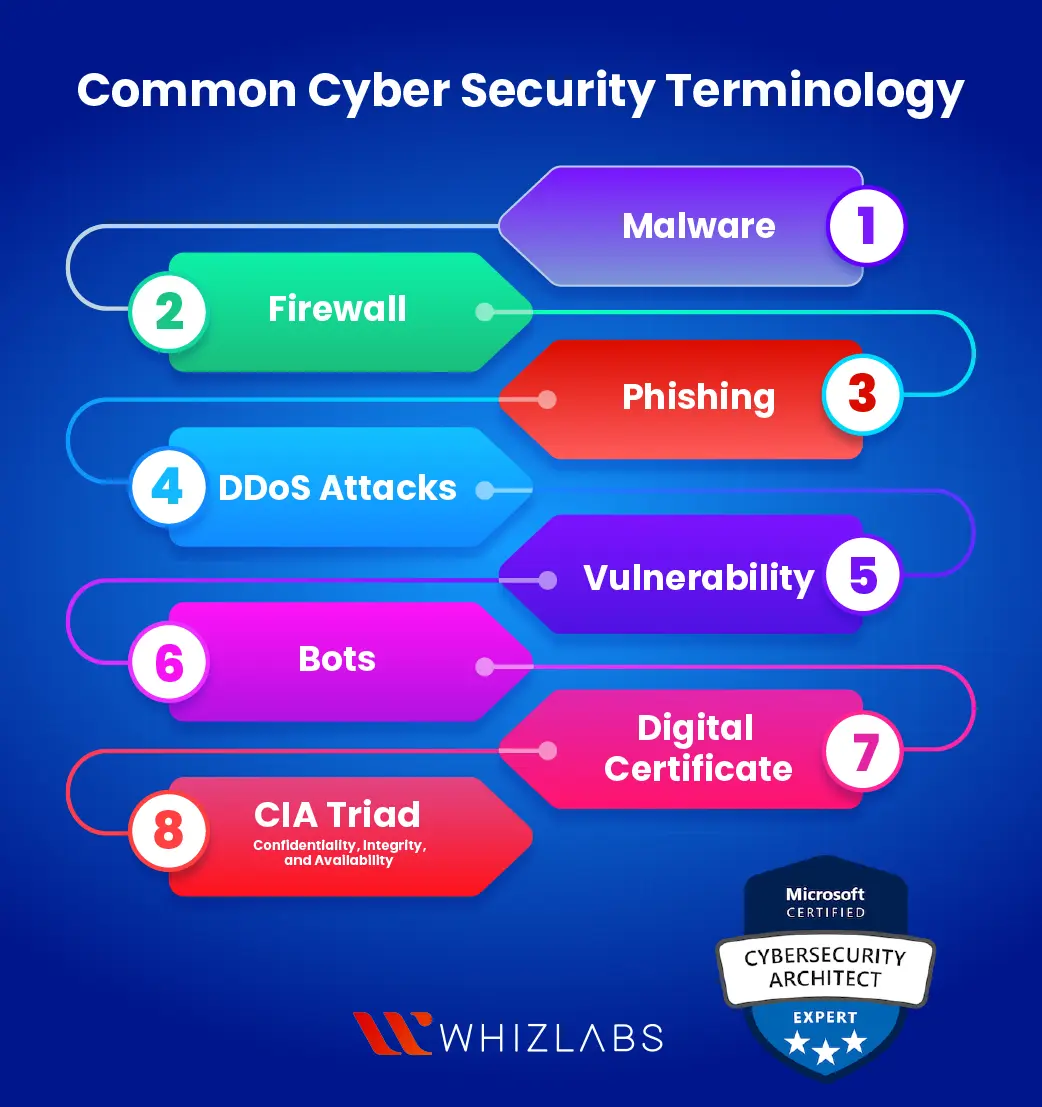 www.whizlabs.com
www.whizlabs.com
Cyber Security Awareness For Parents Infographic | Phishing Tackle
 phishingtackle.com
phishingtackle.com
Cyber Awareness Fy 2024 - Vanni Jaquelin
 minnacathryn.pages.dev
minnacathryn.pages.dev
UIH Cybersecurity - UIH
 www.uih.co.th
www.uih.co.th
UIH CyberSecurity Updated (26 August 2020) - YouTube
 www.youtube.com
www.youtube.com
Department Of Cyber Security And Digital Forensics | Bhubaneswar Campus
 bhubaneswar.nfsu.ac.in
bhubaneswar.nfsu.ac.in
Cybersecurity process improvement: applying lean principles to. Hu places among the 10 best for its cybersecurity offerings. Important cybersecurity terms you should know in 2023