← apa pekerjaan cyber security Apa itu cyber security? ini pengertian, tugas, gaji, dan jenjang latest ioc in cyber security Case studies: successful implementations of ioc in cyber defense →
If you are searching about 5 Components of Information Security you've came to the right web. We have 35 Pics about 5 Components of Information Security like Indicators of Compromise: Cybersecurity’s Digital Breadcrumbs - Hashed, Indicators of Compromise: Cybersecurity’s Digital Breadcrumbs - Hashed and also Mastering IOC Cybersecurity: A Tech Enthusiast Perspective. Here it is:
5 Components Of Information Security
 www.logsign.com
www.logsign.com
Indicators Of Compromise: Cybersecurity’s Digital Breadcrumbs - Hashed
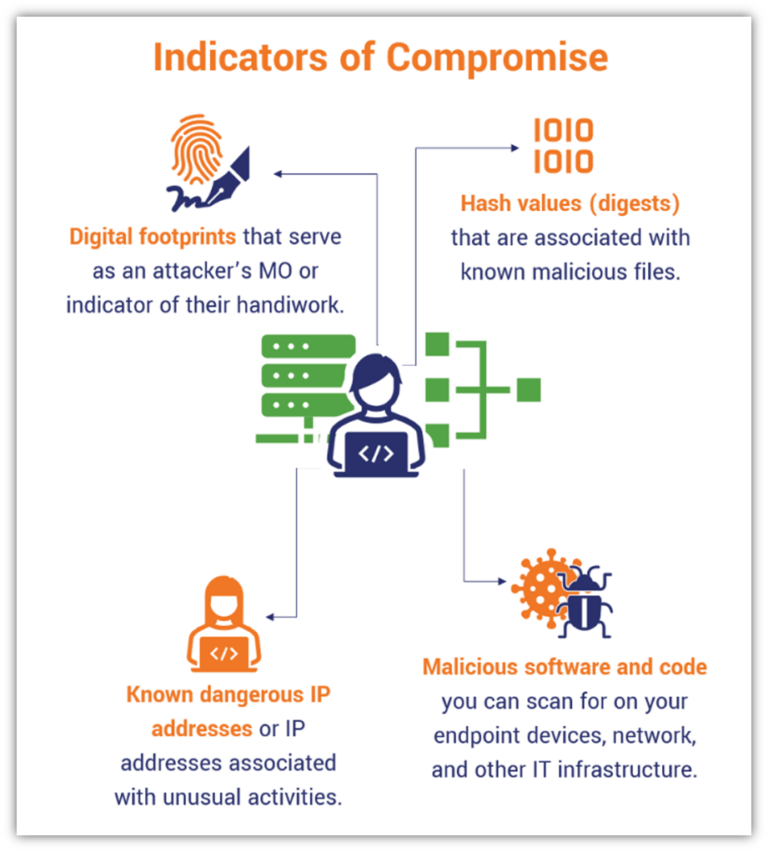 www.thesslstore.com
www.thesslstore.com
Understanding IOCs, Cyber Security News, Threat Intel, And Data Leakage
 www.threatvirus.com
www.threatvirus.com
Indicators Of Compromise (IOCs) – Early Signs Of Cyber Threats
 itsecurity.blog.fordham.edu
itsecurity.blog.fordham.edu
IOAs Und IOCs Im Vergleich | CrowdStrike
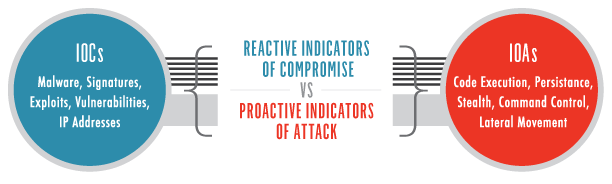 www.crowdstrike.de
www.crowdstrike.de
Mastering IOC Cybersecurity: A Tech Enthusiast Perspective
 cyberexperts.com
cyberexperts.com
What Is Threat Intelligence In Cyber Security?| IOA's And IOC's | TI In
 www.youtube.com
www.youtube.com
IOA Vs IOC In Cyber Defense: Unraveling The Key Distinctions
 www.tatacommunications.com
www.tatacommunications.com
IOC Vs IOA: Indicators Of Threat Intelligence - Security Investigation
 www.socinvestigation.com
www.socinvestigation.com
Cybersecurity IOC Advisory: Understanding And Mitigating The Threat Of
 www.linkedin.com
www.linkedin.com
IOAs Und IOCs Im Vergleich | CrowdStrike
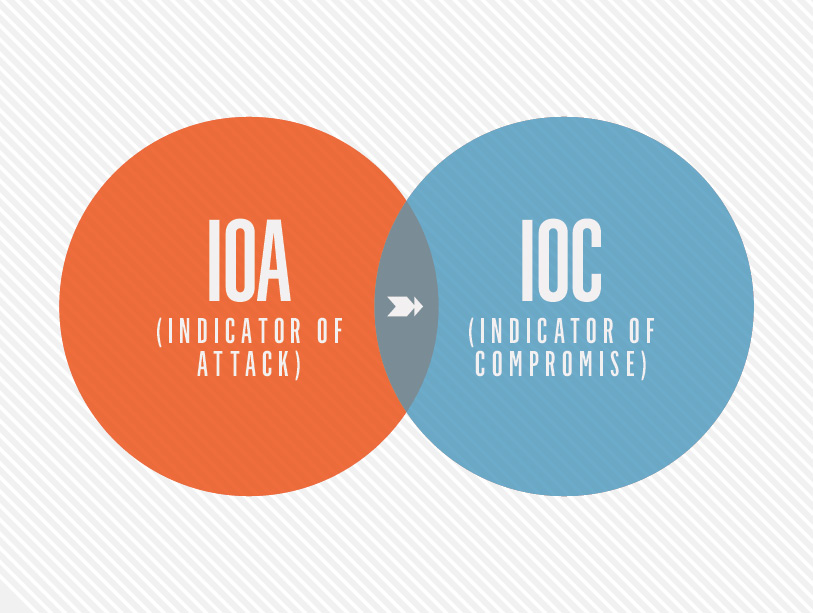 www.crowdstrike.de
www.crowdstrike.de
Indicators Of Compromise (IOCs): How We Collect And Use Them | Securelist
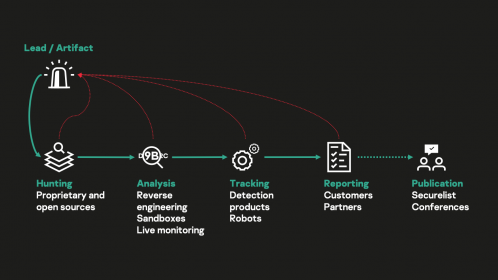 securelist.com
securelist.com
What Are Indicators Of Compromise (IOC) In Cyber Security? - Intellipaat
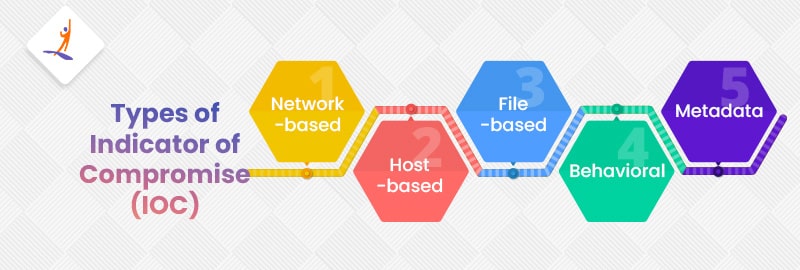 intellipaat.com
intellipaat.com
What Is IOC And IOA In Cyber Security? - Darwin's Data
 darwinsdata.com
darwinsdata.com
The Importance And Difference Of IoC And IoA - Logsign
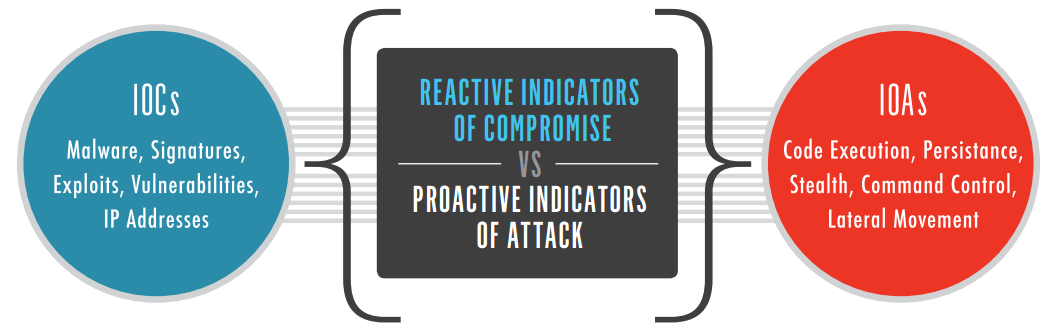 www.logsign.com
www.logsign.com
ioc compromise ioa indicators importance iocs
What Are Indicators Of Compromise? IOC Explained - Zenarmor.com
 www.zenarmor.com
www.zenarmor.com
What Is Indicators Of Compromise (IOC)? - Definition From WhatIs.com
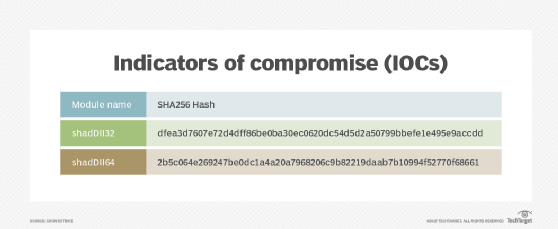 searchsecurity.techtarget.com
searchsecurity.techtarget.com
compromise indicators ioc iocs definition stix
What Is IOC And IOA | Indicator Of Attack And Indicator Of Compromise
 www.youtube.com
www.youtube.com
Unraveling The Complexity: IOC Cybersecurity Explained - CyberExperts.com
 cyberexperts.com
cyberexperts.com
Mastering IOC Cybersecurity: A Tech Enthusiast Perspective
 cyberexperts.com
cyberexperts.com
Indicators Of Compromise: Cybersecurity’s Digital Breadcrumbs - Hashed
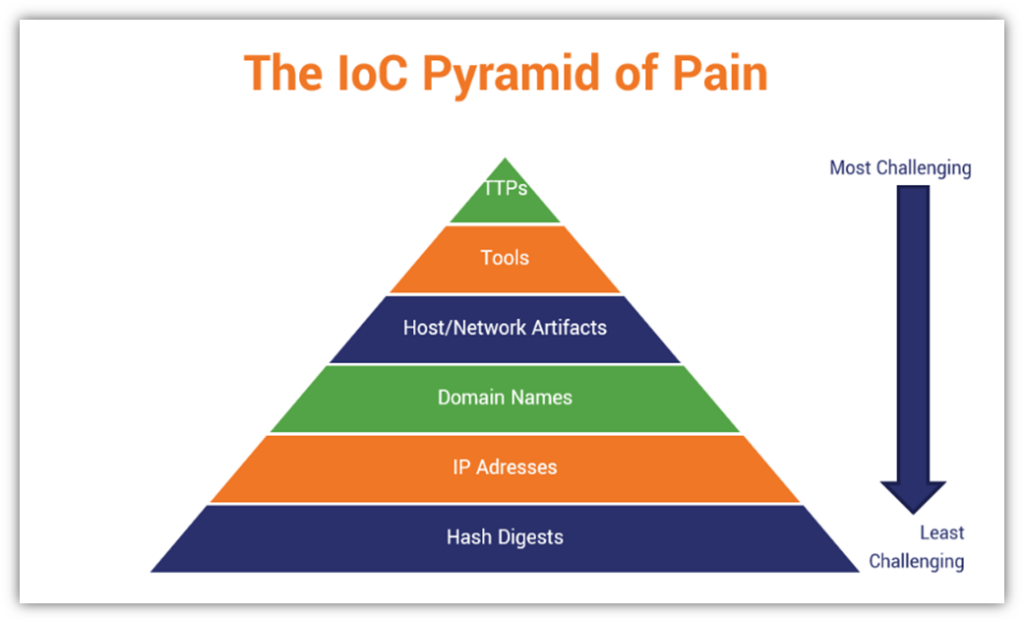 www.thesslstore.com
www.thesslstore.com
Unraveling The Complexity: IOC Cybersecurity Explained - CyberExperts.com
 cyberexperts.com
cyberexperts.com
Unleashing The Power Of IoCs In Cybersecurity
 www.neumetric.com
www.neumetric.com
Indicators Of Compromise: Cybersecurity’s Digital Breadcrumbs - Hashed
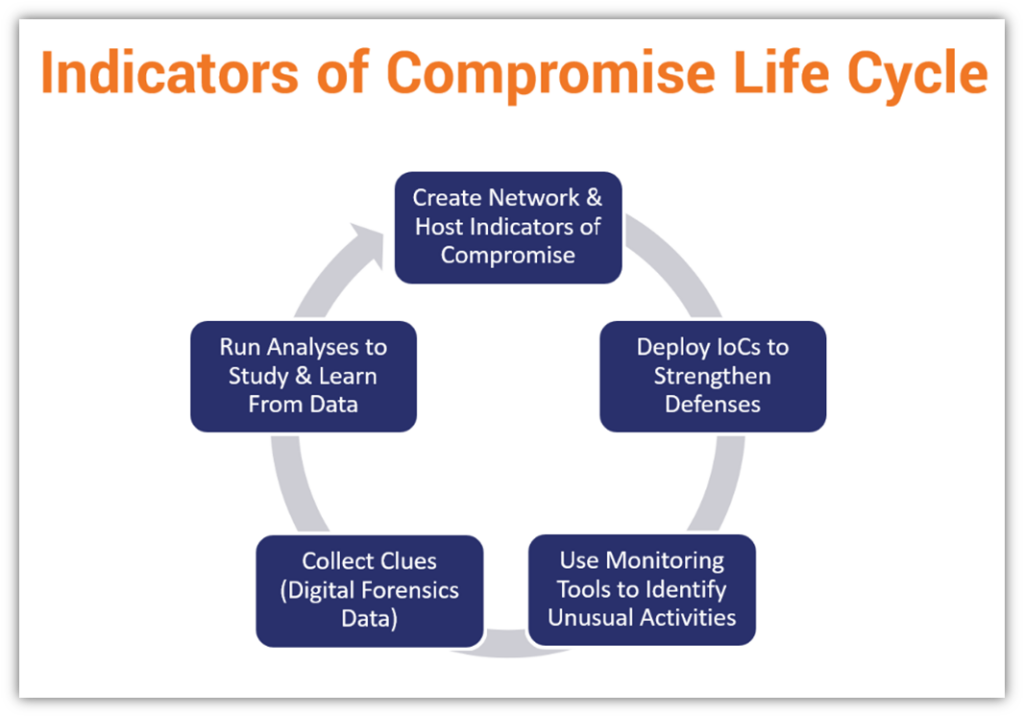 www.thesslstore.com
www.thesslstore.com
Indicator Of Attack Vs Indicator Of Compromises
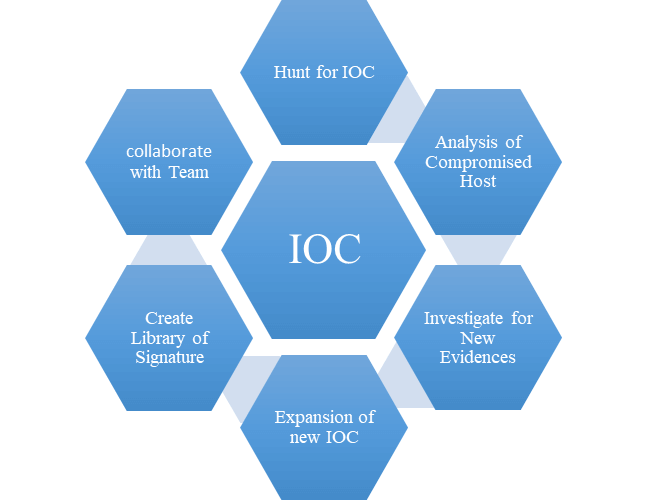 hackforlab.com
hackforlab.com
indicator indicators compromises ioc
What Are Indicators Of Compromise (IOC) In Cyber Security? - Intellipaat
 intellipaat.com
intellipaat.com
What Are Indicators Of Compromise (IOC)?
 www.wallarm.com
www.wallarm.com
IOC Vs IOA | Explained By Cyber Security Professional - YouTube
 www.youtube.com
www.youtube.com
What Are Indicators Of Attack (IOAs)? How They Differ From IOCs | UpGuard
 www.upguard.com
www.upguard.com
Threat Detection: IOC Vs. IOA - RocketCyber
 www.rocketcyber.com
www.rocketcyber.com
Infographic - The Anatomy Of Cybersecurity — Early Adopter
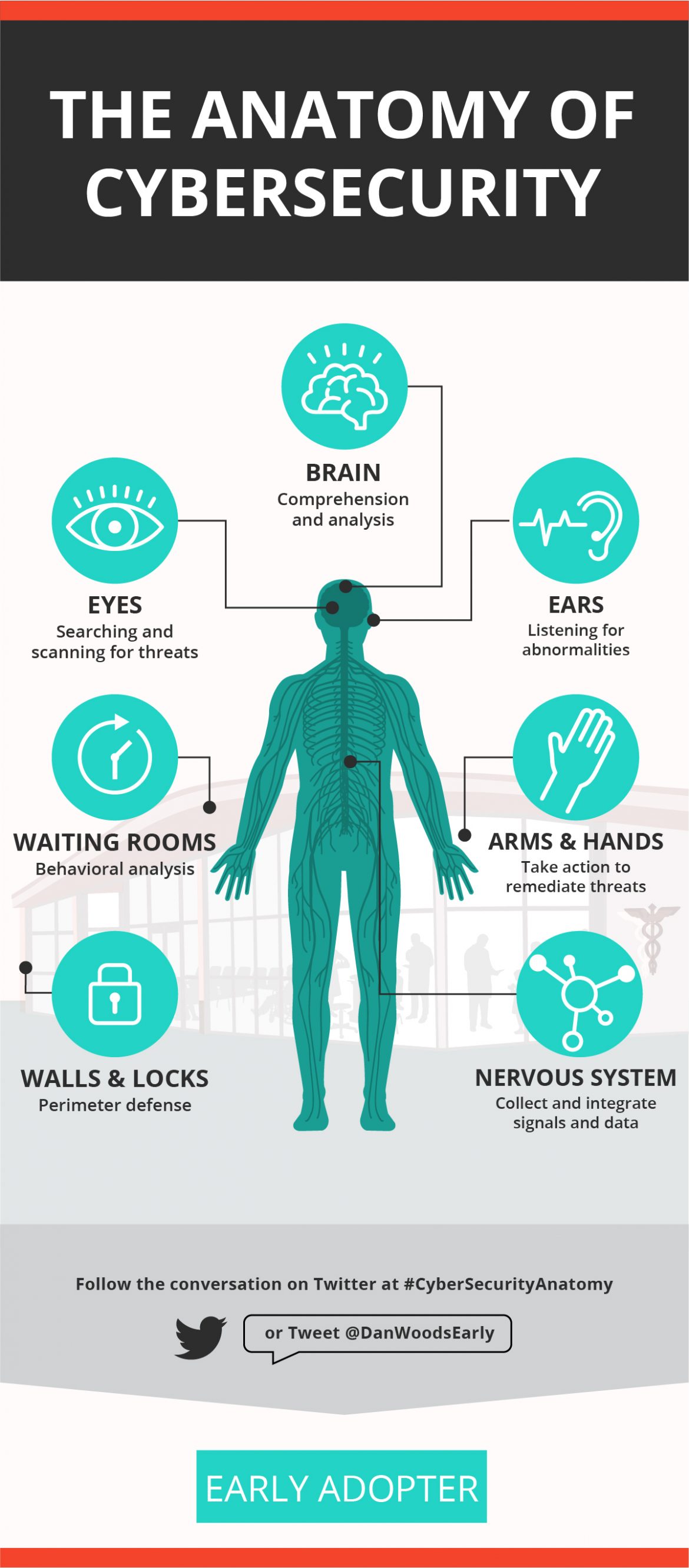 earlyadopter.com
earlyadopter.com
infographic cybersecurity anatomy cyber security functions
Unraveling The Complexity: IOC Cybersecurity Explained - CyberExperts.com
 cyberexperts.com
cyberexperts.com
Indicators Of Compromise (IOCs): How We Collect And Use Them | Securelist
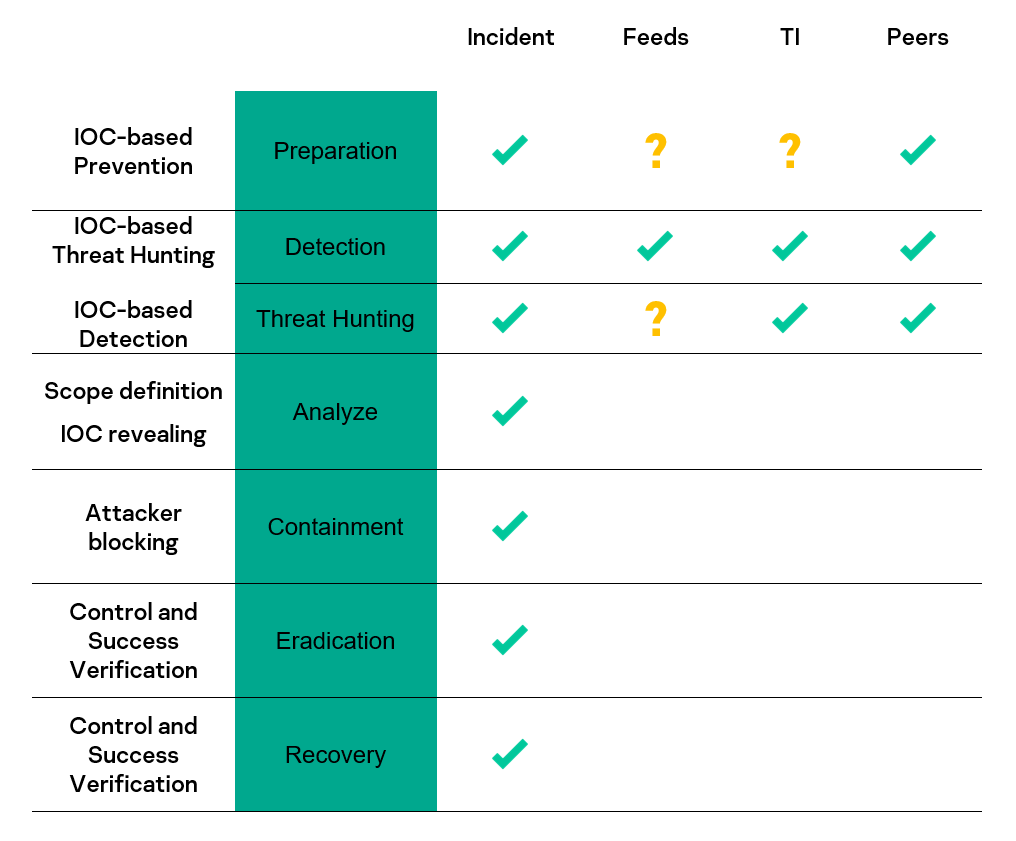 securelist.com
securelist.com
IOC Vs IOA: #1 Cybersecurity Strategy & Threat Intelligence
 blueteamresources.in
blueteamresources.in
IOC Vs IOA: Indicators Of Threat Intelligence - Security Investigation
 www.socinvestigation.com
www.socinvestigation.com
Unraveling the complexity: ioc cybersecurity explained. What are indicators of compromise (ioc) in cyber security?. Threat detection: ioc vs. ioa