← ioc cyber security meaning Indicator indicators compromises ioc what does ioc stand for cyber security What is ioc in cyber security examples? →
If you are looking for Importance of Indicators of Compromise (IoCs) in CTI for Actionable you've came to the right place. We have 35 Pics about Importance of Indicators of Compromise (IoCs) in CTI for Actionable like Cyber Security IOC feeds aggregator - Product Information, Latest, Indicators of Compromise: Cybersecurity’s Digital Breadcrumbs - Hashed and also Known LockBit 3.0 ransomware IOCs and TTPs found in recent assaults, US. Read more:
Importance Of Indicators Of Compromise (IoCs) In CTI For Actionable
 socradar.io
socradar.io
Case Studies: Successful Implementations Of IoC In Cyber Defense | MoldStud
 moldstud.com
moldstud.com
Critical Cybersecurity Threats: 5 Powerful Trends To Master
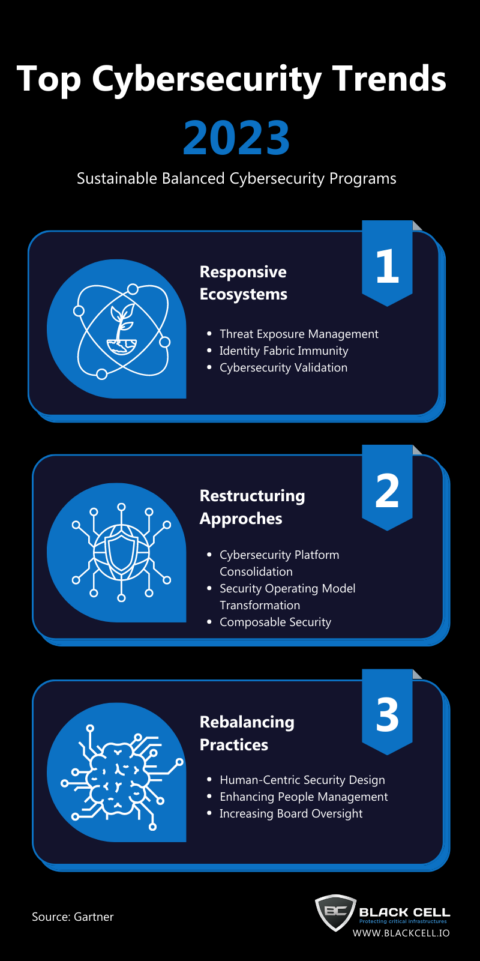 techaku.com
techaku.com
Indicators Of Compromise: Cybersecurity’s Digital Breadcrumbs - Hashed
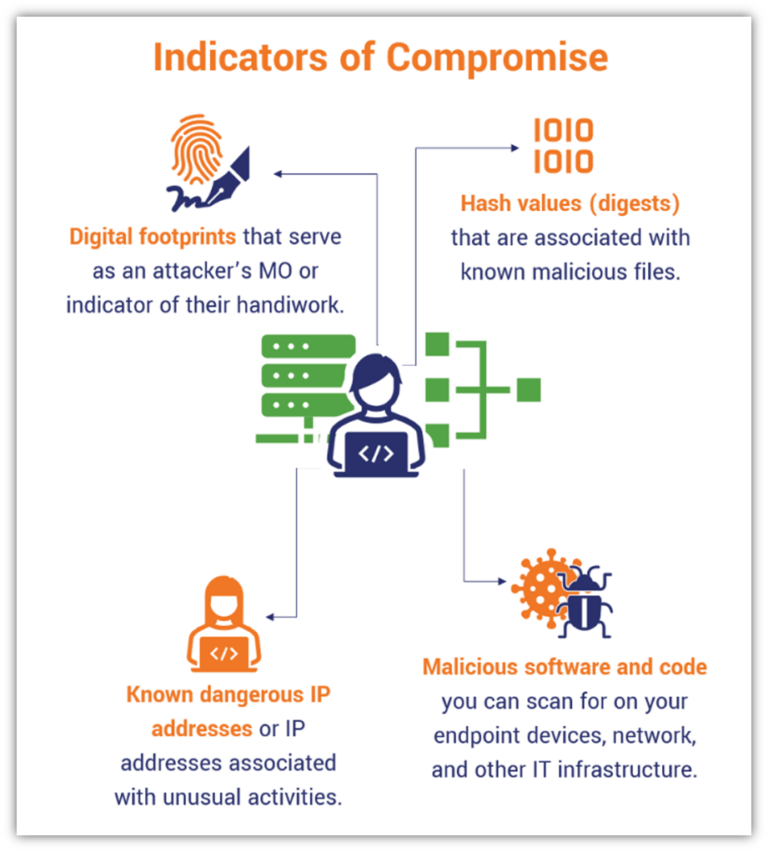 www.thesslstore.com
www.thesslstore.com
Cybersecurity IOC Advisory: Understanding And Mitigating The Threat Of
 www.linkedin.com
www.linkedin.com
IOA Vs IOC In Cyber Defense: Unraveling The Key Distinctions
 www.tatacommunications.com
www.tatacommunications.com
Unleashing The Power Of IoCs In Cybersecurity
 www.neumetric.com
www.neumetric.com
Known LockBit 3.0 Ransomware IOCs And TTPs Found In Recent Assaults, US
 industrialcyber.co
industrialcyber.co
What Is IOC And IOA In Cyber Security? - Darwin's Data
 darwinsdata.com
darwinsdata.com
What Is IOC In Cyber Security? - Logsign
 www.logsign.com
www.logsign.com
ioc compromise indicators
What Are Indicators Of Compromise (IOC) In Cyber Security? - Intellipaat
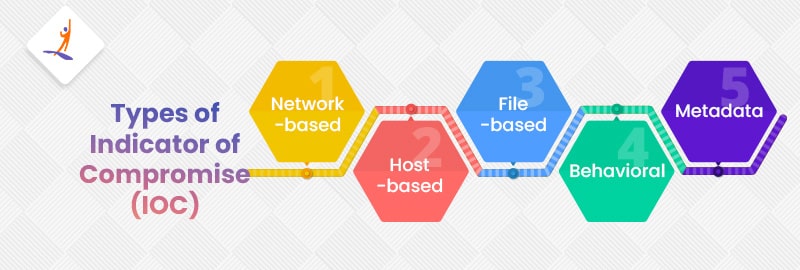 intellipaat.com
intellipaat.com
What Is IOC In Cyber Security Examples? - Darwin's Data
 darwinsdata.com
darwinsdata.com
IOC Vs IOA: Indicators Of Threat Intelligence - Security Investigation
 www.socinvestigation.com
www.socinvestigation.com
Mastering IOC Cybersecurity: A Tech Enthusiast Perspective
 cyberexperts.com
cyberexperts.com
Improve SOC Efficiency With Intelligence-Powered Security Operations
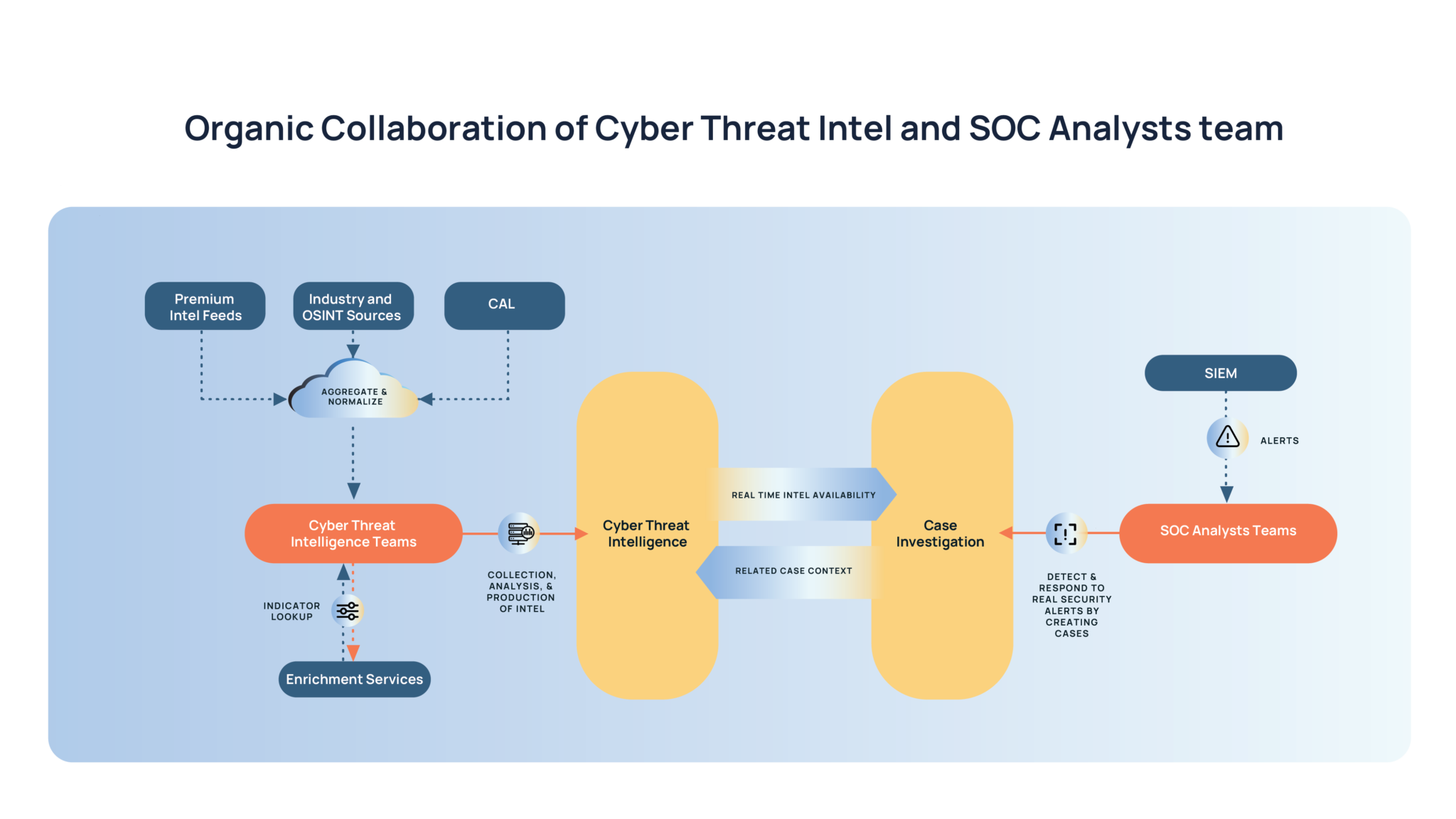 threatconnect.com
threatconnect.com
What Are Indicators Of Compromise (IOC) In Cyber Security? - Intellipaat
 intellipaat.com
intellipaat.com
IOA Vs IOC: What Is The Difference In Cybersecurity?
 www.trio.so
www.trio.so
Importance Of Indicators Of Compromise (IoCs) In CTI For Actionable
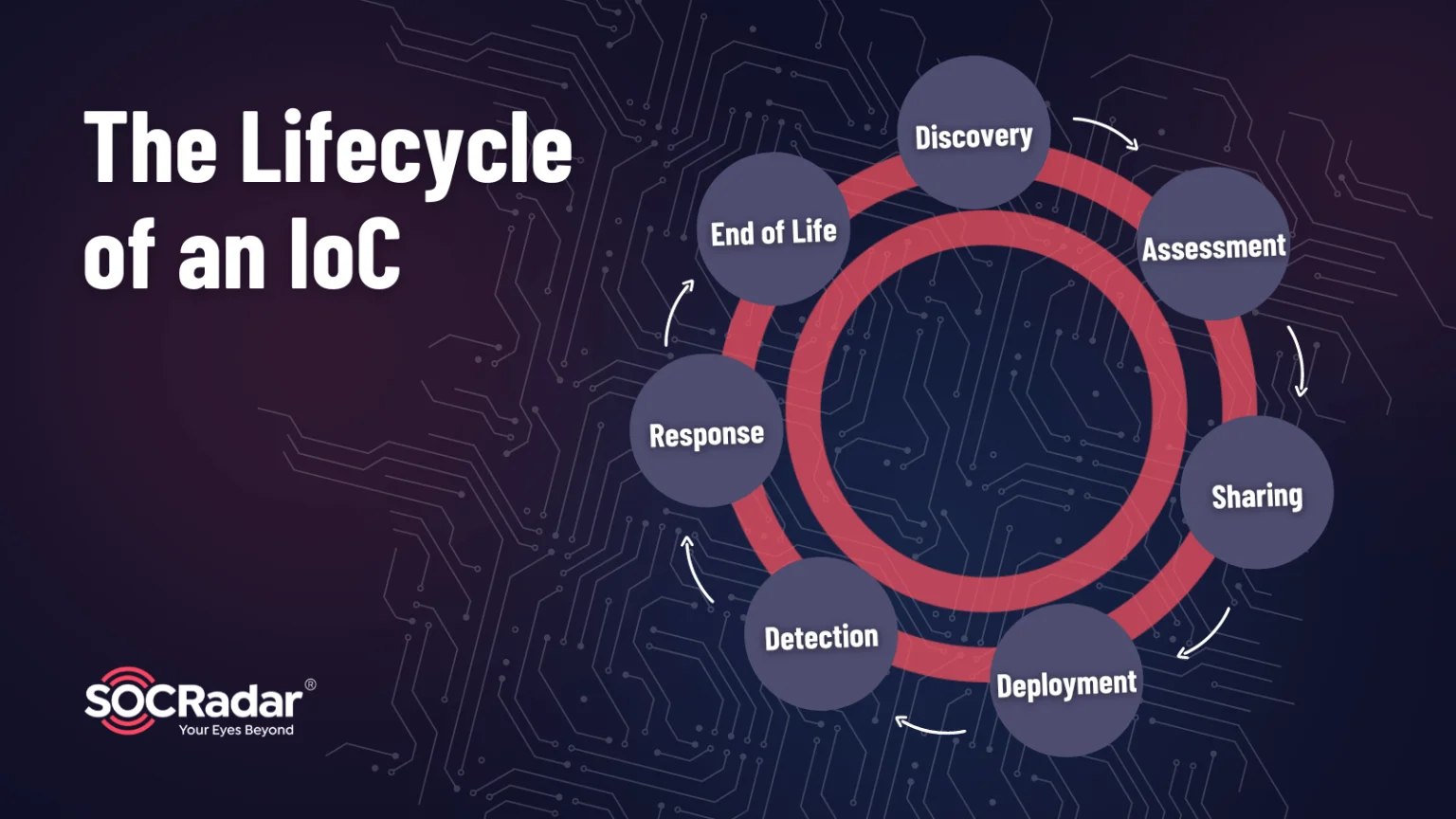 socradar.io
socradar.io
Mastering IOC Cybersecurity: A Tech Enthusiast Perspective
 cyberexperts.com
cyberexperts.com
What Is IOC In Cyber Security: Essential Insights For Staying Secure
 coursedrill.com
coursedrill.com
Mastering IOC Cybersecurity: A Tech Enthusiast Perspective
 cyberexperts.com
cyberexperts.com
What Is Threat Intelligence In Cyber Security?| IOA's And IOC's | TI In
 www.youtube.com
www.youtube.com
What Are Indicators Of Compromise (IOC)?
 www.wallarm.com
www.wallarm.com
Threat Intelligence – Cobalt Strike Stager Latest IOCs - Security
 www.socinvestigation.com
www.socinvestigation.com
threat iocs stager cobalt ioc analyst ransomware kaseya vsa agent tesla malware
Mastering IOC Cybersecurity: A Tech Enthusiast Perspective
 cyberexperts.com
cyberexperts.com
IOA Vs IOC In Cyber Defense: Unraveling The Key Distinctions
 www.tatacommunications.com
www.tatacommunications.com
Unraveling The Complexity: IOC Cybersecurity Explained - CyberExperts.com
 cyberexperts.com
cyberexperts.com
Understanding IOCs, Cyber Security News, Threat Intel, And Data Leakage
 www.threatvirus.com
www.threatvirus.com
Cyber Security IOC Feeds Aggregator - Product Information, Latest
 www.producthunt.com
www.producthunt.com
Unraveling The Complexity: IOC Cybersecurity Explained - CyberExperts.com
 cyberexperts.com
cyberexperts.com
Unraveling The Complexity: IOC Cybersecurity Explained - CyberExperts.com
 cyberexperts.com
cyberexperts.com
IOC Vs IOA | Explained By Cyber Security Professional - YouTube
 www.youtube.com
www.youtube.com
IOC Vs IOA: #1 Cybersecurity Strategy & Threat Intelligence
 blueteamresources.in
blueteamresources.in
Cyber Security – Cyber Security, Networking, Technology Courses And Blog
 practonet.com
practonet.com
What's Indicator Of Compromise (IOC) In Cybersecurity
 blogs.protectedharbor.com
blogs.protectedharbor.com
Improve soc efficiency with intelligence-powered security operations. Mastering ioc cybersecurity: a tech enthusiast perspective. What is ioc and ioa in cyber security?